Since early 2020, remote working has dramatically changed the IT infrastructure of a huge number of organizations across the globe.
While applications and servers remain largely the same, the user-side that requires access has been drastically altered. Users now need to connect across different locations, from external networks that do not have the same strict security protocols as the company network.
In addition, users are relying on more unmanaged devices. As an initial solution, IT leaders may expand their company VPNs; however, this can lead to a very loaded network as well as new user issues and connection difficulties.
The Solution: Zero Trust Security
The massive shift to remote work in the face of Covid-19 proved what many IT and security experts already knew: Network-based access is not secure enough. What is preferable is an identity-based and device-based solution: Zero Trust.
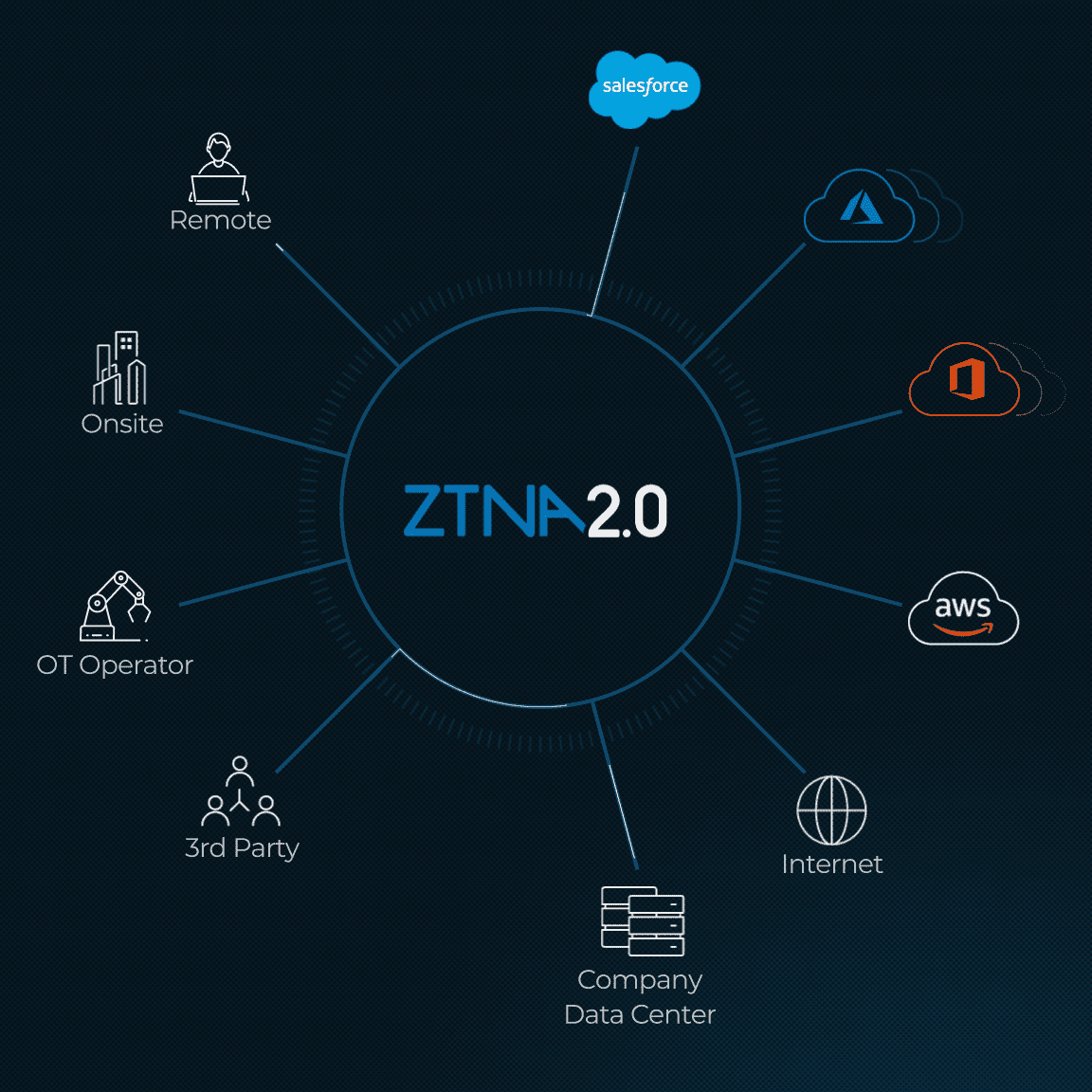
In the Zero Trust model, the traditional parameters used to define secure access, such as the originating network and domain membership, are no longer the decisive ones.
Instead, the Zero Trust approach is based on micro-segmentation of the network, with a focus on the organization’s most valuable data and assets. Every device, user, app and network used to access business data is monitored, managed, secured, and continuously verified. In this environment, remote access is no longer a security problem for IT. What matters is the user ID, not where it came from.
Many companies use enterprise VPN solutions to address the challenges of remote connectivity. However, according to CISA, VPNs might cause data breaches unless they implement multi-factor authentication (MFA) and are regularly patched and updated.
Even if companies continue using a VPN, a Zero Trust architecture could assist when the network is loaded with traffic.